Security Concerns in AWS–Introducing the Amazon Virtual Private Cloud (VPC)
One way to get around all security concerns in AWS is to create what is called a Virtual Private Cloud. A VPC can be considered as an extension of your existing corporate network – with all the instances sitting in AWS. It is a virtual network dedicated to your AWS account.
This lets YOU define all networking layer details – such as which subnets should be external facing (public websites for example), which subnets should be internal, what should the rules be for inbound and outbound communications etc.
Some security features that make Amazon VPCs unique
- Amazon VPC provides security features to enable inbound and outbound filtering at the instance level and subnet level.
- In addition, you can store data in Amazon S3 and restrict access so that it’s only accessible from instances in your VPC.
What about the PUBLIC facing subnet within your VPC?
Anytime you open up your instances to the internet, there is an inherent security risk.
Public facing websites can be categorized by their n-Tiers – are they single tier (Blogs etc. with just a public website and no backend), 2 or more tiers (with backend servers)?
For Single Tier Websites
The configuration for this scenario includes:
- A virtual private cloud (VPC) with JUST a public subnet.
- An Internet gateway to enable communication over the Internet.
A typical configuration might look like:
- An instance with a private IP address in the subnet range (example: 10.0.0.7), which enables the instance to communicate with other instances in the VPC,
- An Elastic IP address (example: 198.51.101.7), which enables the instance to be reached from the Internet.
- For instances in the VPC to communicate over the Internet without having to assign each instance an Elastic IP address, one can use a NAT gateway.
For Multi Tier Websites
- You would simply have a public SUBNET (for the public websites) and private SUBNET (for the backend servers).
- The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the instances in the private subnet cannot.
So then, how does a backend server (like a database server) get important updates (like windows security updates etc.)?
- The private subnet instances can access the Internet by using a NAT (network address translation ) gateway that resides in the public subnet.
- The database servers can connect to the Internet for software updates using the NAT gateway, but the Internet cannot initiate connections to the database servers.
VPC Security through Security Groups
Security Groups act like basic firewalls – controlling the IP addresses and ports that an instance has access to. Security groups can be defined for a group of instances as well as single instances.
In our case, remember, we partitioned our VPC into two subnets – a private subnet (for all the backend servers) and a public subnet (for servers accessible by the internet).
Between the subnets, there needs to be secure communication. This is best accomplished by creating TWO security groups – one containing all the PRIVATE instances – and one containing all the PUBLIC instances. Once this is done, it is easy to set the SOURCE as one security group (say PRIVATE) and the TARGET as the other one (PUBLIC).
Now , there should be trust between the two subnets. This technique avoids having to individually trust machines from one subnet to the other.
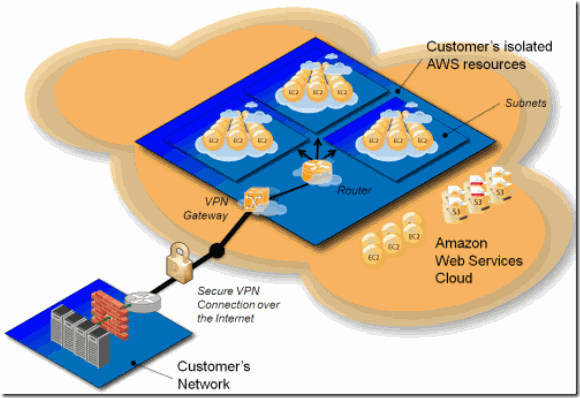
For Additional Security – add a hardware VPN – and Virtual Private Gateway
If you are still concerned about your VPC security, you can add a hardware VPN to route traffic between your corporate network and the private subnet. This way, you can think of the VPC as just an extension of your corporate network.
What about traffic from your network (internal network) to a public facing instance (elastic IP)? Well – normally, it would go over the internet. However, with your VPN Gateway in place, you could instead set up a route to enable your network traffic to go over the virtual private gateway – and onto the public subnet.
Summary
Somehow, ‘the cloud’ conjures up security issues for most people. After all, you are essentially placing your corporate assets in a public, shared environment.
However, to take the PUBLIC out of it, you can create your own PRIVATE cloud – a VPC. This is a very common AWS construct – and is relatively easy to setup.
The VPC comes with the ability to configure INBOUND and OUTBOUND traffic at the instance and the SUBNET level. However, in addition to the built-in capabilities, you can go a step further.
You have a variety of options to make it even more secure – such as NATs, Hardware VPNs and Virtual Private Gateways.
Where can I learn more?
Anuj Varma offers a 1-day seminar covering all emerging technologies.
This seminar includes Cloud Computing, BigData, NoSQL, mobile computing, Javascript Libraries and other customized content not available elsewhere.
All content is based on real-world implementations.
Leave a Reply