Hidden Network in available Wifi Networks
This is not a cause for alarm. All this means is that someone has a network that doesn’t broadcast it’s SSID. Several folks, companies, neighbors may do exactly that, to increase security through obscurity.
Could this also be a man in the middle, trying to get you to inadvertently connect? Sure – but keep in mind that man in the middle attackers would ideally name their network something more friendly – like ‘Starbucks wifi’. Saying ‘hidden network’ is a sure fire way to trigger someone’s suspicion.
In any case, if you would still like to block such hidden networks altogether, follow these steps
Step 1 – Block the hidden network completely
On windows, open a command prompt and type the following command
netsh wlan add filter permission=block ssid="hidden network" networktype=infrastructure
and press Enter. This will not prevent it from showing up in the list – but it will prevent any connection to this ‘hidden network’.
That’s it – that will permanently block any ‘hidden network’ from connecting to your PC. If you see some other suspicious network (such as ‘MyBroadbandNetwork etc.) – do the same thing. Block it by using ‘MyBroadbandNetwork’ in the ssid = above).
Step 2 – Uninstall (whatever network adapter is showing the hidden network) from Device Manager
Also – to remove whatever it is that is allowing this hidden network to show up in the first place, follow these steps:
From a cmd prompt, type:
- set devmgr_show_non-present_devices=1 –> hit Enter
- Start devmgmt.msc (windows device manager) and –> hit Enter
- Click ‘View’ –> Show Hidden Devices
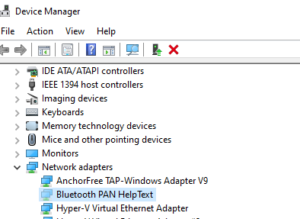
- Next, Expand the Network Adapters tree as shown below. There should be a dimmed adapter (in my case, see Bluetooth PAN help text below).
- Right click this dimmed adapter and ‘Uninstall’
Summary
While seeing a hidden network isn’t a cause for concern, if you would like to block your PC from connecting to these networks entirely, follow the steps above.
Leave a Reply