Azure – VPN Gateway Setup – Virtual Network Gateway
There are three constructs that are needed to setup an Azure VPN Tunnel. These are VPN Gateway (a type of a VNG), a Local Gateway and a Connection.
Virtual network gateway
A virtual network gateway is composed of two or more virtual machines that are deployed to a specific subnet you create, which is called the gateway subnet. The VMs that are located in the gateway subnet are created when you create the virtual network gateway. Virtual network gateway VMs are configured to contain routing tables and gateway services specific to the gateway. You can’t directly configure the VMs that are part of the virtual network gateway and you should never deploy additional resources to the gateway subnet.
Creating a virtual network gateway can take up to 45 minutes to complete. When you create a virtual network gateway, gateway VMs are deployed to the gateway subnet and configured with the settings that you specify. One of the settings you configure is the gateway type. The gateway type ‘vpn’ specifies that the type of virtual network gateway created is a VPN gateway. After you create a VPN gateway, you can create an IPsec/IKE VPN tunnel connection between that VPN gateway and another VPN gateway (VNet-to-VNet), or create a cross-premises IPsec/IKE VPN tunnel connection between the VPN gateway and an on-premises VPN device (Site-to-Site). You can also create a Point-to-Site VPN connection (VPN over IKEv2 or SSTP), which lets you connect to your virtual network from a remote location, such as from a conference or from home.
VPN Gateway
A VPN gateway is a specific type of virtual network gateway that is used to send encrypted traffic between an Azure virtual network and an on-premises location over the public Internet. You can also use a VPN gateway to send encrypted traffic between Azure virtual networks over the Microsoft network. Each virtual network can have only one VPN gateway. However, you can create multiple connections to the same VPN gateway. When you create multiple connections to the same VPN gateway, all VPN tunnels share the available gateway bandwidth.
Local Gateway
A local Gateway (local means on-prem) – is a representation of an on premises router WITHIN azure. Azure takes all the info it needs from the on prem router – and configures a Virtual Device (local Gateway) within Azure.
Connection (of Type – Site to Site)
Once you have the VPN Gateway and Local Gateway Configured in Azure, all we need is a ‘Connection’ between the two. From ‘All Resources’ – Add (search for connection). That connection type should be a Site-to-Site (not VPN-to-VPN). Pick any shared secret key that you can remember. That’s all there is to it.
What the Customer Needs to Do
Once the Connection Step has been completed, Azure will display a Connection Details Screen. From this screen, you can download the configuration file for the on-premises router (Azure will auto detect the router type based on the Public IP of the router, provided by the customer).
Confusing Public IPs
This is where most of the confusion occurs. There are two public IPs that you need to worry are
1) The public IP of the customer’s VPN Router. This comes from the customer and is fed into the ‘Local Gateway’ creation step in Azure.
2) The public IP of the VNG that Azure creates. This IP is assigned by Azure – and is visible once the VNG is provisioned. This is needed for the Customer to enter into their router’s configuration (it is automatically part of the downloaded configuration file)
Upgrade , Downgrade VPN Type
It is best to use Powershell (and Azure Cloud Shell) to accomplish this. Say you want to downgrade to ‘Basic’
PS C:\>$Gateway = Get-AzureRmVirtualNetworkGateway -Name “MyVirtualGateway”
PS C:\> Resize-AzureRmVirtualNetworkGateway -VirtualNetworkGateway $Gateway -GatewaySku “Basic”
Summary and Troubleshooting
For AWS users, these three steps may seem a little confusing. However, once you set up this VPN Tunnel on Azure, it will seem intuitive to create the local Gateway and create a Connection between the local Gateway and the VPN Gateway.
HealthChecks and Troubleshooting Azure Site to Site VPN
There are two things you need to check to ensure that the VPN Tunnel is ‘Connected’.
1. Simply look at the ‘Connection’ in Azure Portal. If it says ‘Connected’ – and you see the inbound data increasing, that is an indication that all is set up correctly.
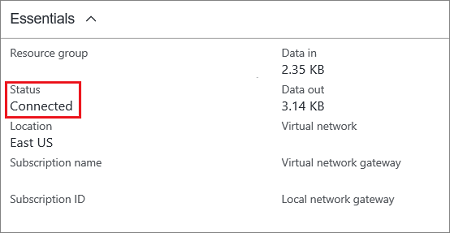
2. A quick healthcheck on the Azure side of things – Healthcheck : https://<YourVirtualNetworkGatewayIP>:8081/healthprobe
Troubleshooting Guide
Leave a Reply